[15-Oct-2017]: Updated the installation steps and web portal configuration steps to support pfSense v2.4.
Introduction
I wanted to build a virtual lab environment at home that would emulate an office environment. My requirements were to have separate network segments for Clients & Servers, and two DMZ networks. I also wanted my home network, which is external to the virtual lab environment, to emulate the Internet, even though it really isn’t.
VMware Workstation has a feature called LAN Segments. LAN Segments are a great way to create private virtual networks for any number of uses, but keep in mind that you cannot use Workstation’s DHCP features with LAN Segments.
This means you become responsible for defining a LAN segment’s IP addressing by configuring static IPs on the VMs connected to the segment, and if you want to connect multiple LAN segments together, you need a VM that can provide routing between the LAN segments.
The following is how I created multiple “named” LAN segments within VMware Workstation, and routed between them using a VM running pfSense, which is an open source firewall.
Planning the Network Segments & the pfSense vNICs
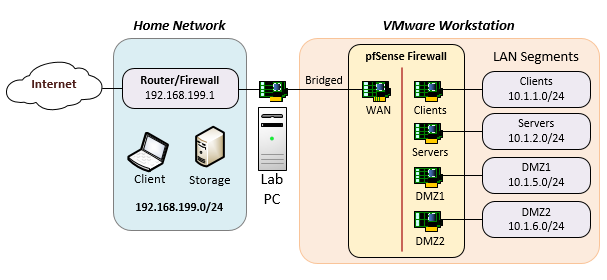
My lab PC is a tower with a single physical NIC connected to my home network (Home-Net), which uses an address space of 192.168.199.0/24.
I reserved 192.168.199.101 – 192.168.199.110 for my lab environment to use as external “public” IPs, and I made sure my Home-Net DHCP service was not giving out IPs in that range.
When creating the VM for the pfSense firewall, the first virtual NIC (vNIC) will be “bridged” to Home-Net. After installing pfSense, this vNIC will be configured as pfSense’s WAN interface, and given the following settings:
- Static IP: 192.168.199.101/24
- Upstream Gateway: 192.168.199.1
The upstream gateway is the router/firewall shown in the Home Network section of the above diagram. This configuration allows lab VMs to access the Internet through the pfSense firewall. All network traffic leaving the lab that is not assigned a NAT IP within pfSense will get sent out using the IP of the WAN interface (PAT).
The below table outlines the IP address plan for each of the lab’s network segments, and includes the pfSense interface names along with the IP addresses that will be assigned to each pfSense interface. The first row shows pfSense’s WAN interface, which as discussed above, will be bridged within VMware Workstation to Home-Net.
| Segment Name | Segment Network |
Interface Name | Interface IP |
|---|---|---|---|
| WAN | 192.168.199.0/24 | em0 -> WAN | 192.168.199.101 |
| Clients | 10.1.1.0/24 | em1 -> LAN | 10.1.1.1 |
| Servers | 10.1.2.0/24 | em2 -> OPT1 | 10.1.2.1 |
| DMZ1 | 10.1.5.0/24 | em3 -> OPT2 | 10.1.5.1 |
| DMZ2 | 10.1.6.0/24 | em4 -> OPT3 | 10.1.6.1 |
Download pfSense
Download the latest pfSense full installer:
- Architecture: AMD64 (64-bit)
- Platform: CD Image (ISO) Installer
- Mirror: [Pick the one that’s closest to you]
If needed, use 7-Zip to extract the ISO from the archive file.
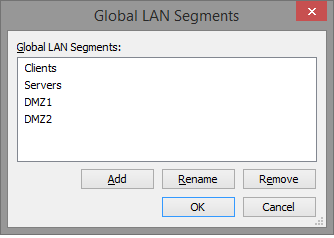
Creating the LAN Segment Names
From within VMware Workstation, open the settings of any existing VM, and select the VM’s network adapter.
- Click on the LAN Segments button, add the following segment names, and click OK.
- Clients
- Servers
- DMZ1
- DMZ2
Create the pfSense VM in VMware Workstation
New Virtual Machine
- Custom (Advanced)
- Hardware Compatibility: Workstation 10.x, Workstation 11.x, or Workstation 12.x
- Install From: I will install the operating system later
- Select a Guest Operating System: Other > FreeBSD 64-bit
- Virtual Machine Name: pfSense-FW
- Processors
- Number of Processors: 1
- Number of Cores per Processor: 1
- Memory for this Virtual Machine: 512 MB
- Network Connection: Use Bridged Networking
- SCSI Controller: LSI Logic (Recommended)
- Virtual Disk Type: IDE (Recommended)
- Create a New Virtual Disk
- Max Disk Size: 5 GB
- Store Virtual Disk as a single file
Edit Virtual Machine Settings
- Sound Card: Remove
- USB Controller: Clear All Selections
- CD/DVD: Use ISO Image File, and browse to the PfSense ISO file
(Optional) Disable Unnecessary Ports & Controllers
- VM > Power > Power On to BIOS or Power On to Firmware
- Advanced (tab) > I/O Device Configuration
- Serial Port A: Disabled
- Serial Port B: Disabled
- Parallel Port: Disabled
- Floppy Disk Controller: Disabled
- Exit Saving Changes
Install pfSense
Note: After installing pfSense and doing the initial configuration, these instructions finish the configuration via the pfSense web portal. To follow along, you will need a Windows or Linux VM so you can connect to the web portal with a browser (Firefox, Chrome, Edge, etc.).
Installing from the ISO Image
- Power on the VM.
- On the welcome screen choose: 1. Boot Multi User [Enter]
- Or allow the timer to expire.
- Copyright and Distribution Notice: Accept [Enter]
- Welcome screen (Install should already be selected): OK [Enter]
- Keymap Selection (“Standard US” is the default). If needed, choose a Keymap, then Select [Enter]
- Partitioning: Auto (UFS) Guided Disk Setup
- Manual Configuration: NO
- Reboot
Disconnect the ISO image file from the CD/DVD drive while rebooting, and wait for the prompt to configure the WAN interface (em0).
WAN Interface Assignment
Should VLANs be set up now [y|n]? n Enter the WAN interface name or 'a' for auto-detection (em0 or a): em0 Enter the LAN interface name or 'a' for auto-detection NOTE: This enables full Firewalling/NAT mode. ( a or nothing if finished): <ENTER> The interfaces will be assigned as follows WAN -> em0 Do you want to proceed [y|n]? y
After assigning the WAN interface, pfSense will configure itself. When it’s done, you’ll be presented with a list of options. Directly above the list you’ll see the configuration for the WAN interface. If you have DHCP enabled in your home network, the WAN interface will get an IP address, but we will assign a static IP later.
Power off the pfSense VM (Halt System).
Enter an Option: 6 pfSense will shutdown and halt system. This may take a few minutes, depending on your hardware. Do you want to proceed [y|n]? y
Add Additional vNICs to the pfSense VM
Edit the virtual machine settings:
- Hardware (tab) > Add > Network Adapter
- NAT: Used to share the host’s IP address
- Connect at power on should be selected
- Finish
- NAT: Used to share the host’s IP address
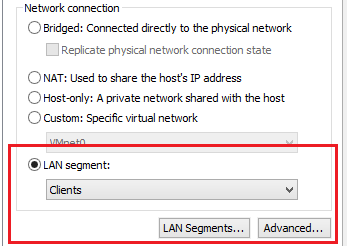
- Make sure the new network adapter is selected, and make the following changes:
- Select: LAN Segment (radio button)
- From the drop-down menu choose the Clients LAN segment
- Click the Advanced button, click Generate to create a MAC address
- Document the MAC address and LAN Segment name
- Click OK
Repeat adding a new vNIC for the Servers, DMZ1, and DMZ2 LAN Segments.
When you’re done, you should have documentation that shows each vNIC’s MAC address associated with a LAN Segment name. You want this in case things get confusing when setting up each vNIC in pfSense. Here’s an example:
| LAN Segment Name | MAC Address |
|---|---|
| Clients | 00:50:56:2C:E7:D2 |
| Servers | 00:50:56:38:DD:36 |
| DMZ1 | 00:50:56:38:BF:16 |
| DMZ2 | 00:50:56:20:B8:B2 |
Configure the New Interfaces in pfSense
Power on the pfSense VM, and wait for it to boot.
Assign Interfaces
Enter an option: 1
Valid interfaces are:
em0 00:0c:29:40:47:37
em1 00:50:56:2C:E7:D2
em2 00:50:56:38:DD:36
em3 00:50:56:38:BF:16
em4 00:50:56:20:B8:B2
Note the listing of interface names and their MAC addresses. They should match up accordingly.
- em0 = WAN Interface (Bridged)
- em1 = Clients (LAN Segment)
- em2 = Servers (LAN Segment)
- em3 = DMZ1 (LAN Segment)
- em4 = DMZ2 (LAN Segment)
Should VLANs be set up now [y|n]? n Enter the WAN interface name or 'a' for auto-detection: em0 Enter the LAN interface name or 'a' for auto-detection NOTE: this enables full Firewalling/NAT mode. (em1 em2 em3 em4 a or nothing if finished): em1 Enter the Optional 1 interface name or 'a' for auto-detection (em2 em3 em4 a or nothing when finished): em2 Enter the Optional 2 interface name or 'a' for auto-detection (em3 em4 a or nothing when finished): em3 Enter the Optional 3 interface name or 'a' for auto-detection (em4 a or nothing when finished): em4 Enter the Optional 4 interface name or 'a' for auto-detection ( a or nothing when finished): <ENTER> The interfaces will be assigned as follows: WAN -> em0 LAN -> em1 OPT1 -> em2 OPT2 -> em3 OPT3 -> em4 Do you want to proceed [y|n]? y
Set the WAN Interface IP Address
Note: If you’re building your lab in a laptop that will be connecting to various networks, you’ll want to skip this step, and just let the WAN interface get its IP address configuration from DHCP. You will also want to change the VM’s vNIC setting from Bridged to NAT.
Enter an option: 2 Enter the number of the interface you wish to configure: 1 Configure IPv4 address WAN interface via DHCP? (y/n) n Enter the new WAN IPv4 address. Press <ENTER> for none: > 192.168.199.101 Subnet masks are entered as bit counts (as in CIDR notation) in pfSense. e.g. 255.255.255.0 = 24 255.255.0.0 = 16 255.0.0.0 = 8 Enter the new WAN IPv4 subnet bit count (1 to 31): > 24 For a WAN, enter the new WAN IPv4 upstream gateway address. For a LAN, press <ENTER> for none: > 192.168.199.1 Configure IPv6 address WAN interface via DHCP6? (y/n) n Enter the new WAN IPv6 address. Press <ENTER> for none: > <ENTER> Do you want to revert to HTTP as the webConfigurator protocol? (y/n) y Please wait while the changes are saved to WAN... Reloading filter... Reloading routing configuration... DHCPD... Restarting webConfigurator... The IPv4 address has been set to 192.168.199.101/24 Press <Enter> to continue. <ENTER>
You should now see the following above the list of options:
WAN (wan) -> em0 -> v4: 192.168.199.101/24 LAN (lan) -> em1 -> OPT1 (opt1) -> em2 -> OPT2 (opt2) -> em3 -> OPT3 (opt3) -> em4 ->
Set the LAN Interface IP Address
Enter an option: 2 Enter the number of the interface you wish to configure: 2 Enter the new LAN IPv4 address: > 10.1.1.1 Subnet masks are entered as bit counts (as in CIDR notation) in pfSense. e.g. 255.255.255.0 = 24 255.255.0.0 = 16 255.0.0.0 = 8 Enter the new LAN IPv4 subnet bit count (1 to 31): > 24 For a WAN, enter the new LAN IPv4 upstream gateway address. For a LAN, press <ENTER> for none: > <ENTER> Enter the new WAN IPv6 address. Press <ENTER> for none: > <ENTER> Do you want to enable DHCP server on LAN? (y/n) n Do you want to revert to HTTP as the webConfigurator protocol? (y/n) y Please wait while the changes are saved to LAN... Reloading filter... Reloading routing configuration... DHCPD... The IPv4 LAN address has been set to 10.1.1.1/24 You can now access the webConfigurator by opening the following URL in your web browser: http://10.1.1.1/ Press <ENTER> to Continue. <ENTER>
You should now see the following above the list of options:
WAN (wan) -> em0 -> v4: 192.168.199.101/24 LAN (lan) -> em1 -> v4: 10.1.1.1/24 OPT1 (opt1) -> em2 -> OPT2 (opt2) -> em3 -> OPT3 (opt3) -> em4 ->
The IP address for the LAN interface becomes the URL for the web management portal (webConfigurator).
Switch to a Windows or Linux client VM that has its vNIC assigned to the Clients LAN Segment, and configure the OS with an IP and mask on the same network. For example:
- IP Address: 10.1.1.15
- Mask: 255.255.255.0
- Gateway: 10.1.1.1
Open a browser, and enter: http://10.1.1.1
- User: admin
- Pass: pfsense
First time logging in? pfSense has a wizard that you can go through. I prefer to skip this by clicking on the logo in the top-left corner.
Troubleshooting Connection Issues
- In the pfSense VM settings, make sure the MAC address of the Clients vNIC matches up to the MAC address shown for the em1 interface.
- In the pfSense console, use option 1 and/or 2 to reconfigure the WAN & LAN interfaces.
- Make sure the vNIC for the Windows/Linux client VM is assigned to the Clients LAN Segment.
- If needed, start over by shutting down the pfSense VM, opening the VM’s settings, and re-adding all of the vNICs, or try generating new MAC addresses for each vNIC.
pfSense Web Mgmt Configuration Tasks
System Tasks
- Click the pfSense logo to skip the configuration wizard.
- System > General Setup
- Hostname: [Enter an appropriate hostname]
- Domain: [Enter an appropriate domain name]
- DNS Servers: [Leave blank or enter an Internet DNS server’s IP address]
- Time Zone: [Leave the default, or select an appropriate time zone]
- NTP Time Server: [Leave the default, or enter your favorite NTP pool of servers]
- Save
- Interfaces > WAN
- Verify the settings, and if needed, make changes.
- Even if you don’t make any changes, click Save
- Click Apply Changes to reset the WAN interface so it can use the DNS settings made on the General Setup page.
- System > Package Manager > Available Packages (tab)
- Search for Open-VM-Tools (click the + Install button, and the Confirm button to install)
- Wait for the Success message in the log window before continuing.
- System > User Manager
- Edit the admin account and set your own super-secret password.
- Diagnostics > Reboot
- The reboot is needed to initialize the Open VM Tools.
Configure the Interfaces
- Interfaces > LAN
- Description: Clients
- Save
- Interfaces > OPT1
- Enable Interface
- Description: Servers
- IPv4 Configuration Type: Static IPv4
- Static IPv4 Address: 10.1.2.1/24
- Save
- Interfaces > OPT2
- Enable Interface
- Description: DMZ1
- IPv4 Configuration Type: Static IPv4
- Static IPv4 Address: 10.1.5.1/24
- Save
- Interfaces > OPT3
- Enable Interface
- Description: DMZ2
- IPv4 Configuration Type: Static IPv4
- Static IPv4 Address: 10.1.6.1/24
- Save
- Apply Changes
Configure the Firewall Rules
These rules are configured with a lab environment in mind. By default, pfSense allows anything connected to its LAN interface (Clients LAN Segment) to access the WAN (Home-Net & Internet), and all of the other network segments.
We will create rules that can block the Clients network segment from accessing the WAN and other networks, but we will leave them disabled. They will be there just in case it’s needed.
We will also allow any Home-Net IP address to ping the WAN address. This can help with troubleshooting.
WAN Firewall Rules
- Firewall > Rules > Wan (tab)
- Click the “Add Rule to the end of the list” button to add a new rule

- Action: Pass
- Interface: WAN
- Address Family: IPv4
- Protocol: ICMP
- ICMP Subtypes: Echo Request
- Source Type: Network
- Source Address: 192.168.199.0 / 24
- Destination Type: WAN address
- Description: Allow Echo requests from Home-Net
- Save
- Click the “Add Rule to the end of the list” button to add a new rule
Clients Firewall Rules
- Firewall > Rules > Clients (tab)
- Click the Garbage Can icon
 in the “IPv6 *” Default allow LAN to any rule to delete it.
in the “IPv6 *” Default allow LAN to any rule to delete it. - Click the “Add rule to the top of the list” button to add a new rule

- Action: Block
- Disabled: Disable this rule
- Interface: CLIENTS
- Address Family: IPv4
- Protocol: Any
- Source Type: Clients net
- Destination Type: SERVERS net
- Description: Block Any to Servers
- Save
- Click the Copy icon
 in the rule you just created to create a new rule based off of that rule.
in the rule you just created to create a new rule based off of that rule. - Make these changes
- Destination Type: DMZ1 net
- Description: Block Any to DMZ1
- Save
- Click the Copy icon
 in the rule you just created to create a new rule based off of that rule.
in the rule you just created to create a new rule based off of that rule. - Make these changes
- Destination Type: DMZ2 net
- Description: Block Any to DMZ2
- Save
- Click the Copy icon
 in the rule you just created to create a new rule based off of that rule.
in the rule you just created to create a new rule based off of that rule. - Make these changes
- Destination Type: WAN net
- Description: Block Any to Home-Net
- Save
- Click the Garbage Can icon
Servers Firewall Rules
- Firewall > Rules > Servers (tab)
- Click the “Add rule to the top of the list” button to add a new rule

- Action: Block
- Disabled: Disable this rule
- Interface: SERVERS
- Address Family: IPv4
- Protocol: Any
- Source Type: SERVERS net
- Destination Type: CLIENTS net
- Description: Block Any to Clients
- Save
- Click the Copy icon
 in the rule you just created to create a new rule based off of that rule.
in the rule you just created to create a new rule based off of that rule. - Make these changes
- Destination Type: DMZ1 net
- Description: Block Any to DMZ1
- Save
- Click the Copy icon
 in the rule you just created to create a new rule based off of that rule.
in the rule you just created to create a new rule based off of that rule. - Make these changes:
- Destination Type: DMZ2 net
- Description: Block Any to DMZ2
- Save
- Click the Copy icon
 in the rule you just created to create a new rule based off of that rule.
in the rule you just created to create a new rule based off of that rule. - Make these changes:
- Destination Type: WAN net
- Description: Block Any to WAN
- Save
- Click the “Add Rule to the end of the list” button to add a new rule

- Action: Pass
- Interface: SERVERS
- Address Family: IPv4
- Protocol: Any
- Source Type: SERVERS net
- Destination Type: Any
- Description: Allow Servers Net to Any
- Save
- Click the “Add rule to the top of the list” button to add a new rule
DMZ1 Firewall Rules
- Firewall > Rules > DMZ1 (tab)
- Click the “Add rule to the top of the list” button to add a new rule

- Action: Block
- Interface: DMZ1
- Address Family: IPv4
- Protocol: Any
- Source Type: DMZ1 net
- Destination Type: CLIENTS net
- Description: Block Any to Clients
- Save
- Click the Copy icon
 in the rule you just created to create a new rule based off of that rule.
in the rule you just created to create a new rule based off of that rule. - Make these changes:
- Destination Type: SERVERS net
- Description: Block Any to Servers
- Save
- Click the Copy icon
 in the rule you just created to create a new rule based off of that rule.
in the rule you just created to create a new rule based off of that rule. - Make these changes:
- Destination Type: DMZ2 net
- Description: Block Any to DMZ2
- Save
- Click the “Add Rule to the end of the list” button to add a new rule

- Action: Allow
- Interface: DMZ1
- Address Family: IPv4
- Protocol: Any
- Source Type: DMZ1 net
- Destination Type: Any
- Description: Allow DMZ1 to Any
- Save
- Click the “Add rule to the top of the list” button to add a new rule
DMZ2 Firewall Rules
- No Rules. You can build your own as needed.
Apply Firewall Rules and Reset State
- Firewall > Rules > Apply Changes
- Diagnostics > States > Reset States (tab) > Reset
- Click on the States (tab). You should see an entry for the VM connected to the pfSense web portal.
Open a command prompt on your lab computer, and try to ping the IP address of the pfSense WAN interface: 192.168.199.101
WAN Virtual IPs and 1:1 NAT
At some point you will want to use the other IPs you reserved on Home-Net (192.168.199.102 – 192.168.199.110) for exposing a lab VM’s services. For example, you build a Web server or Reverse Proxy in DMZ1.
Note: If you built your lab in a laptop, and you configured the pfSense WAN interface to get its IP configuration using DHCP, be careful with your choice of virtual IPs. You don’t want to cause an IP conflict on the external network.
Assign a Home-Net Virtual IP to the WAN Interface
- Firewall > Virtual IPs > Virtual IPs (tab)
- Click “+” to add a new Virtual IP
- Type: IP Alias
- Interface: WAN
- IP Address: <Available Home-Net IP Address> / 24
- Description: <Your Description>
- Save
- Apply Changes
- Click “+” to add a new Virtual IP
Configure a 1:1 NAT Rule
You’re going to map the external Home-Net virtual IP address you created above to the IP address of the internal lab VM.
- Firewall > NAT > 1:1 (tab)
- Click the “Add mapping to the top of the list” button

- Interface: WAN
- External Subnet IP: <Home-Net Virtual IP Address>
- Internal IP Type: Single Host
- Internal IP Address: <Lab VM’s IP Address>
- Description: <Your Description>
- Save
- Apply Changes
- Click the “Add mapping to the top of the list” button
WAN Firewall Rule
This rule will allow you to ping the internal lab VM using the external Home-Net virtual IP address you configured above.
- Firewall > Rules > WAN (tab)
- Click the “Add rule to the top of the list” button to add a new rule

- Action: Pass
- Interface: WAN
- Address Family: IPv4
- Protocol: ICMP
- ICMP Subtypes: Echo Request
- Source Type: WAN Net
- Destination Type: Single host or alias
- Destination Address: <Lab VM’s IP Address>/31
- Description: Allow Echo requests to <Hostname>
- Save
- Apply Changes
- Click the “Add rule to the top of the list” button to add a new rule
Summary
At this point, you’ll want to build some servers and clients to use the LAN Segments you configured in VMware Workstation.
Assuming you’re starting from scratch, and you have a well equipped computer for your lab, here’s a list of things to consider building:
- 2-3 clients with various operating systems.
- Windows Domain Controllers or Linux Samba servers configured as DCs.
- A DHCP server for the Clients network.
- An NTP server to be an authoritative time source for your internal servers.
- A DNS server in DMZ1 to provide external DNS services to external client machines in Home-Net.
- A Web server in DMZ1 to show off your JavaScript, PHP, and HTML5 skills.
- A Microsoft Exchange 2013 environment with a CAS proxy server in DMZ1.
- A Microsoft Lync 2013 environment with an Edge server using DMZ1 & DMZ2.
- A reverse proxy server using DMZ1 & DMZ2 in front of a Microsoft SharePoint environment.
- Add another LAN Segment to VMware Workstation, and use it for replication between a cluster of Exchange mailbox servers or Microsoft SQL 2014 servers.