Three Network Topology Options
Because DirectAccess in Server 2012 R2 can be configured with a single NIC, there are actually more than three network topology options. However, I will only be covering the options when using 2 NICs.
A DirectAccess server supports being behind a NAT device such as a firewall, but it can also be placed directly on the Internet (Edge). Therefore, there are two types of topology configurations: NAT & Edge.
Additionally, most enterprise environments have at least one DMZ network, and a DMZ network should always be used with a DirectAccess server. If there are 2 DMZ networks available, they should both be used in a NAT configuration.
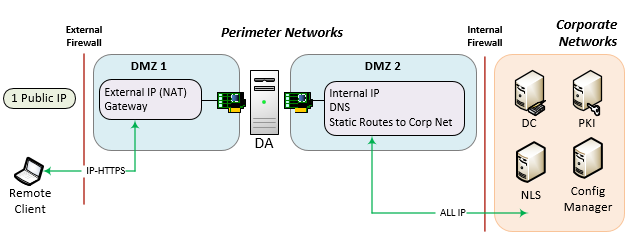
NAT Configuration 1
- 2 NICs (External & Internal)
- Each NIC is in its own DMZ
- By placing the internal NIC in a DMZ, traffic from the DA server can be inspected, and if needed, blocked from accessing the internal corporate resources.
- Very Secure
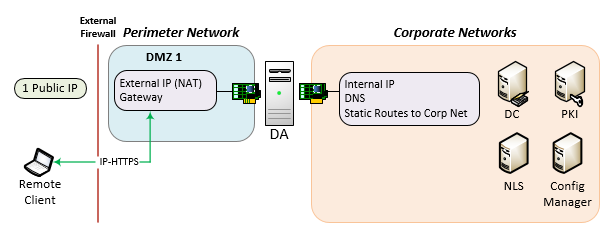
NAT Configuration 2
- 2 NICs (External & Internal)
- External NIC is in a DMZ
- Internal NIC is on the corporate network
- With the internal NIC on the corporate network, traffic from the DA server cannot be inspected or blocked from the internal corporate resources. The only way to stop traffic from the DA server is to stop the services on the DA server, disconnect the internal NIC, or shut the server down.
- Secure
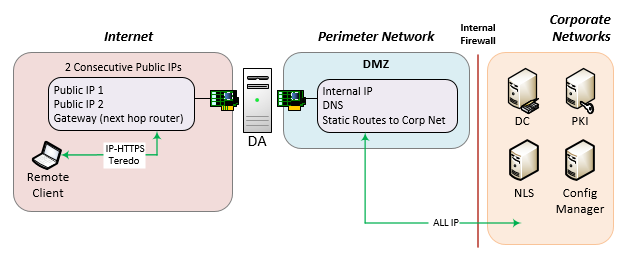
Edge Configuration
- 2 NICs (External & Internal)
- External NIC is connected directly to the Internet (NIC has 2 consecutive public IPs)
- Internal NIC is in a DMZ
- By placing the internal NIC in a DMZ, traffic from the DA server can be inspected, and if needed, blocked from accessing the internal corporate resources.
- Secure